Network Settings
Click or tap the Preferences button to open the Preferences window. Choose the Network tab.
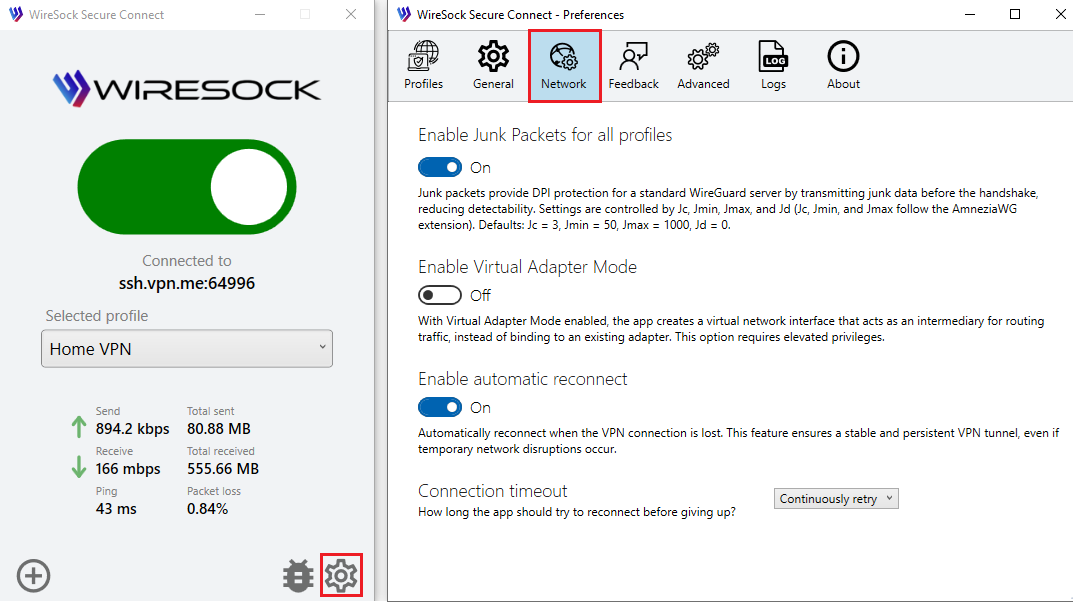
Enable Junk Packets for all profiles
Junk packets are a DPI protection approach that works with a generic WireGuard server. This method allows the transmission of junk packets before the WireGuard handshake, making WireGuard traffic less detectable by DPI systems. The junk packet settings are determined by the Jc, Jmin, Jmax, and Jd parameters (Jc, Jmin, and Jmax correspond to the AmneziaWG protocol extension). The default values are Jc = 3, Jmin = 50, Jmax = 1000 and Jd=0.
This option enables junk packets for all profiles using the default values. You can specify individual parameters per profile on the profile edit tab.
TCP Socket Termination
This feature closes all existing TCP sockets on your system when the VPN connects, based on the profile settings for tunneled apps and networks. Administrator privileges are required.
Some apps keep ongoing connections to certain IP addresses. When the VPN connects, those connections might stay open and continue sending data outside the VPN. This means your real IP address could still be exposed, even though the VPN is active. Turning on this feature closes all existing connections when the VPN starts, helping to prevent any data leaks.
TCP Socket Termination only terminates connections routed through the tunnel based on the split-tunneling settings.
Enable Virtual Adapter Mode
WireSock Virtual Adapter Mode creates a dedicated virtual network interface to handle VPN traffic, offering better isolation, compatibility, and control. Unlike Transparent Mode, which intercepts traffic at the packet level, Virtual Adapter Mode uses a standard network interface, enhancing compatibility with certain applications. However, it requires administrator privileges to create and manage the virtual adapter. In contrast, Transparent Mode has a lower system impact and does not require administrative access.
See more details about Virtual Adapter and Transparent mode in a separate article.
This setting can be configured per profile on the profile edit tab. If explicitly set in the profile, the profile setting takes precedence; otherwise, the global setting is used.
Bypass LAN Traffic
The "Bypass LAN Traffic" option in WireSock Secure Connect allows your computer to communicate with other devices on your local network (LAN) even when the VPN is active. This is especially useful for accessing shared resources such as printers, file servers, or media devices like Chromecast.
When enabled, this option ensures that traffic to and from local IP ranges—including IPv4 link-local addresses, multicast groups, and private networks defined by RFC1918—is excluded from the VPN tunnel. This allows local devices to remain accessible while all other traffic is routed through the VPN.
By default, LAN traffic is blocked when the VPN is active to enhance security and prevent unwanted access on shared or public networks. Enabling this option is recommended only in trusted network environments.
This setting can be configured per profile on the profile edit tab. If explicitly set in the profile, the profile setting takes precedence; otherwise, the global setting is used.
NOTE
DNS requests still go through the VPN, so local hostnames may not resolve. Use IP addresses instead.
Which networks are excluded?
Local network addresses (RFC 1918, RFC 4193)
- 10.0.0.0/8
- 172.16.0.0/12
- 192.168.0.0/16
- 100.64.0.0/10
- fd00::/8
- 169.254.0.0/16
- ff02::/16
- 224.0.0.0/24
- 169.254.0.0/16
- fe80::/10
- 224.0.0.0/4
- ff00::/8
Enable automatic reconnect
Automatically reconnect when the VPN connection is lost. This feature ensures a stable and persistent VPN tunnel, even if temporary network disruptions occur.
Connection timeout
How long the app tries to connect to a VPN server before giving up. If set to Continuous Retry, the app retries indefinitely. Available options:
- 10 sec
- 30 sec
- 1 min
- 2 min
- Continuous Retry