Connection Profiles
A WireGuard profile is the configuration text file (.conf) used to set up and define the parameters of a WireGuard VPN connection. It contains the necessary information to establish a secure connection between devices or peers, such as cryptographic keys, network settings, and other connection details.
WireGuard's configuration is typically divided into two main sections: [Interface] and [Peer]. See details about configuration file structure here.
How to Get Your Connection Profile
You need a connection profile to connect to an WireGuard protocol-compatible VPN server or service. This file contains the directives, parameters, and keys required to establish the client-server VPN connection.
Below, you'll find the options for getting your connection profile.
Using a VPN at work?
Your organization might use a WireGuard server. If you installed WireSock Secure Connect at the request of your IT department, contact them for instructions. They'll help you obtain your connection profile.
Using an WireGuard VPN service or private server?
Request WireGuard configuration file from your VPN provider or check WireGuard site to understand how to configure your own WireGuard server and get config with client's profile.
Working with connection profiles
Wiresock Secure Connect allows to import, edit and delete connection profile.
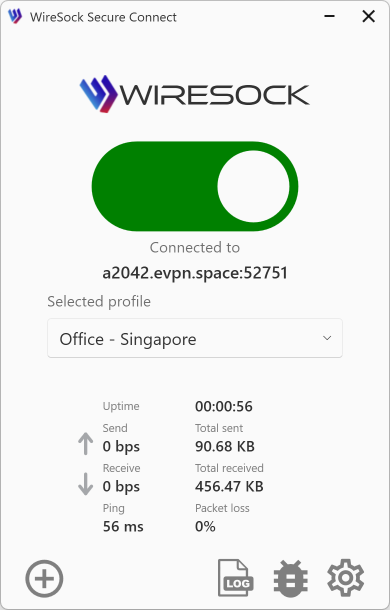
Select the connection profile using the combo box in the main window, the context menu in the profile list, or by double-clicking the profile name.
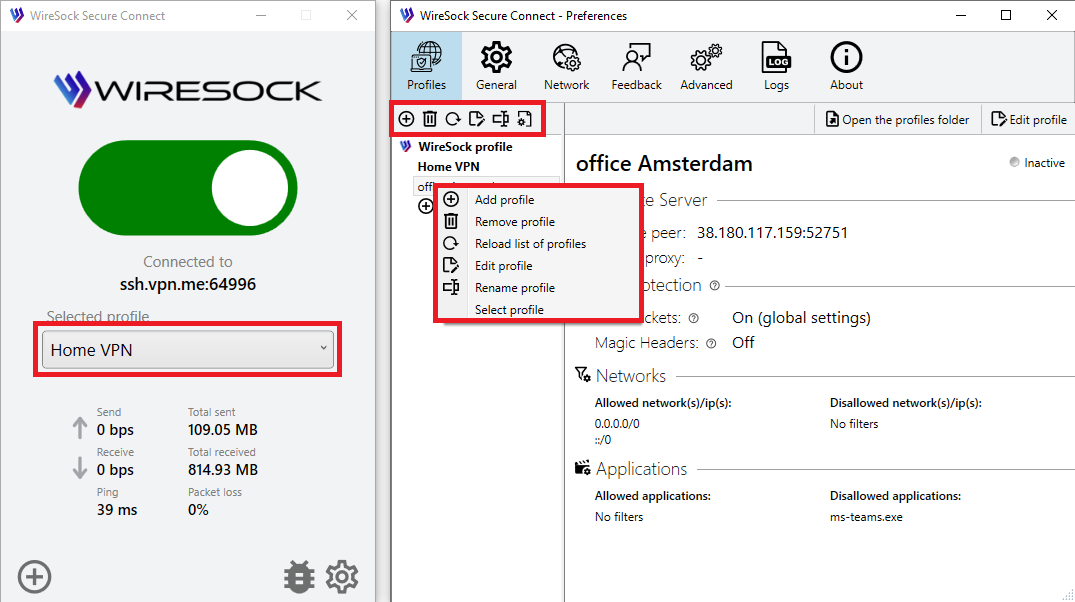
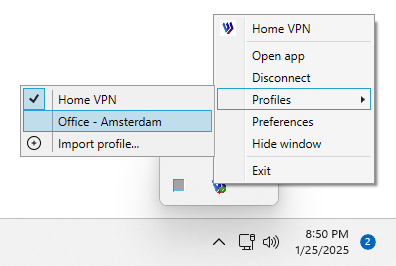
The selection of the connection profile is also available in the system tray context menu.
Import a Profile
You must import a connection profile to connect to a WireGuard server with WireSock Secure Connect from a file downloaded to your device.
To establish a connection to a server, you can import a connection profile file into WireSock Secure Connect by browsing for the file, or dragging and dropping it. Follow the steps below for the process of your choice.
- Obtain the WireGuard .conf file from the VPN server or provider.
- Save it to a location on your device.
- Launch WireSock Secure Connect.
- Click on Import profile icon
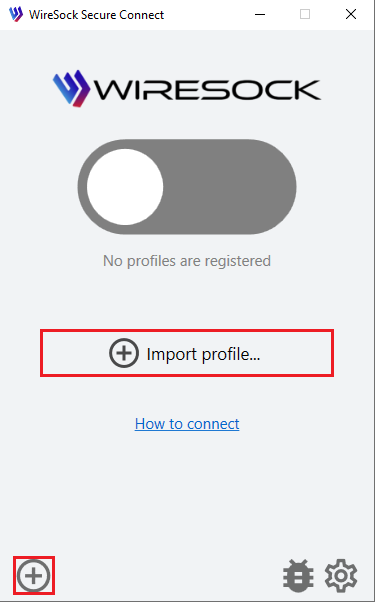
- The Import Profile screen appears.

- Click Browse to navigate to the .conf file and upload.
- or drag and drop your .conf file to the screen.
- The Imported Profile screen displays with the profile name, server hostname and port
Remove a profile
To remove a profile:
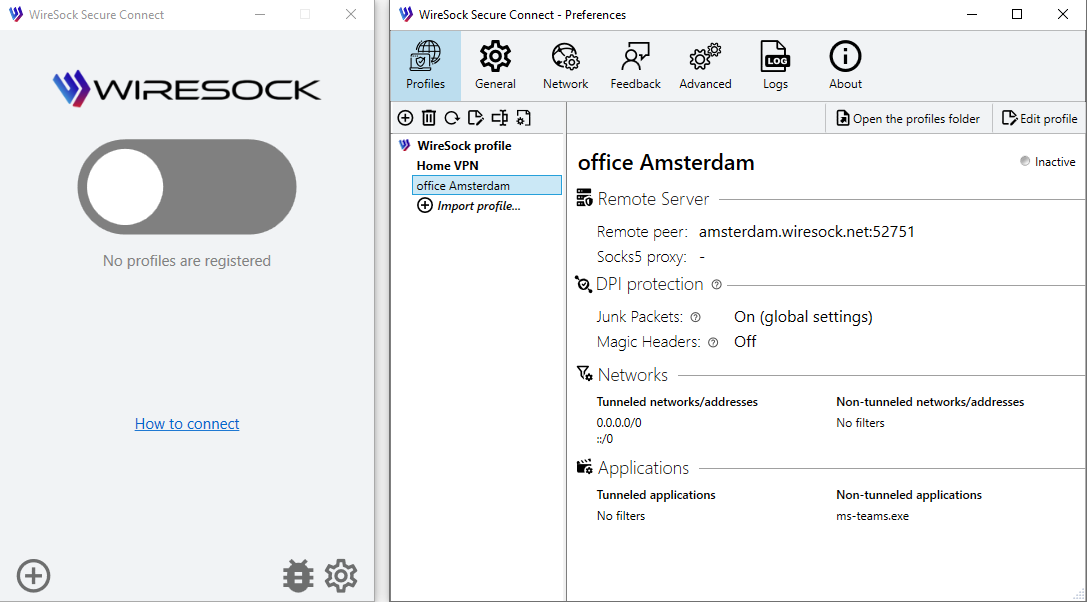
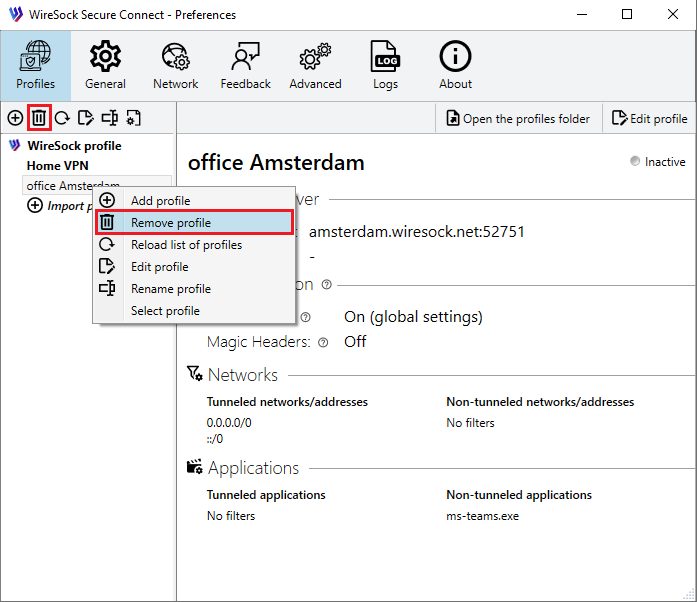
Click the Preferences button to open the Preferences window and select the Profiles tab.
Select the profile you want to remove and press the Remove button or use the context menu.
Edit a profile
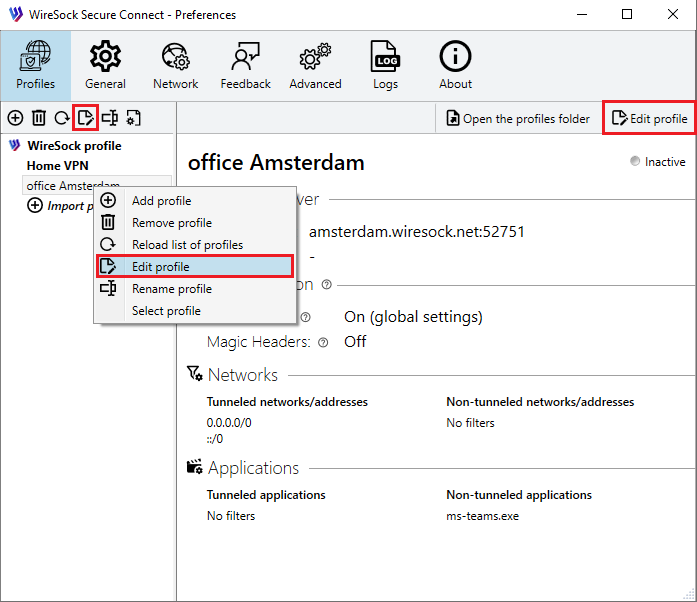
Click the Preferences button to open the Preferences window and select the Profiles tab.

Select the profile that you want to edit and press 'Edit' button at toolbar or button on profile window or use context menu at profiles list:
In the Profile Edit window, you can modify standard WireGuard parameters such as remote peers, DNS, and more, as well as advanced settings specific to WireSock Secure Connect.
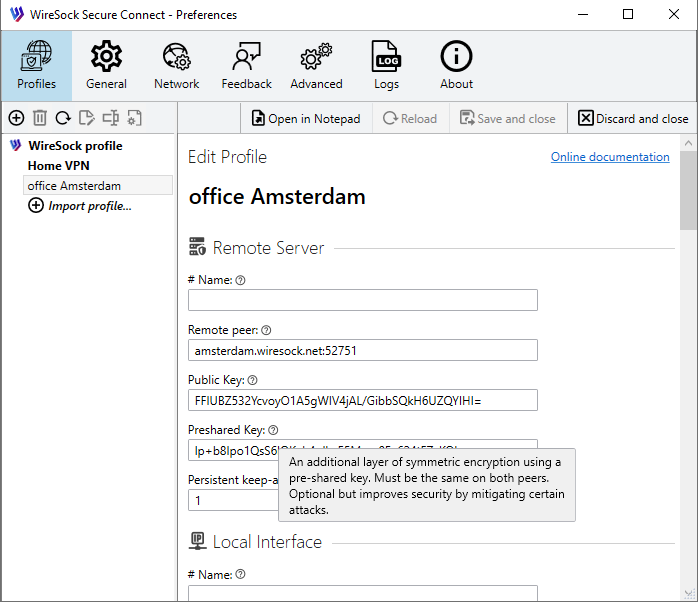
Below is a detailed description of each parameter.
Remote Server
This section defines configuration for remote peers (other WireGuard interfaces you are connecting to).
Name (optional):
- This is just a standard comment in INI syntax used to help keep track of which config section belongs to which node, it's completely ignored by WireGuard and has no effect on VPN behavior.
Remote peer (required):
- Description: The hostname or IP address and port of the remote peer. Required for peers that are not initiating connections.
- Purpose: Specifies where to send encrypted packets.
- Dynamic IPs: If the remote peer has a dynamic IP, consider using a dynamic DNS service.
- Example:
ini Endpoint = vpn.example.com:51820
PublicKey (required):
- Description: The public key of the remote peer, encoded in base64. Used for encrypting traffic to that peer.
- Purpose: Identifies the remote peer and encrypts data sent to it.
- Obtaining the Key: Should be securely shared by the remote peer.
- Example:
ini PublicKey = Ae4TbZPdsXPUrbIjkItC3aJ7bDtx4OCDfz7eS5Nh9ho=
PresharedKey (optional):
- Description: An additional layer of symmetric encryption using a pre-shared key. Must be the same on both peers.
- Purpose: Adds an extra layer of symmetric encryption.
- Generation: Can be generated using
wg genpsk. - Usage: Must be shared securely and set identically on both peers.
- Example:
ini PresharedKey = 6vqAaV2V5EnpNi5AqfZ57EKbQq8+OXRa5gAh+yOcRw=
PersistentKeepalive (optional):
- Description: Sends keepalive packets at the specified interval (in seconds) to maintain NAT mappings. Useful for peers behind NAT.
- Purpose: Maintains NAT mappings on routers/firewalls that may drop idle connections.
- Recommended Value:
25seconds is commonly used. - Example:
ini PersistentKeepalive = 25
Local interface
This section defines settings for the local WireGuard interface, including network configurations and cryptographic keys.
PrivateKey (required)
- Description: The private key of the local interface, encoded in base64. This key must remain secret.
- Purpose: Essential for establishing encrypted communication. Must be kept confidential.
- Generation: Can be generated using
wg genkey. - Usage: This key is specific to the local machine and should not be shared.
- Example:
ini PrivateKey = 6vAaW2V5EnpNi5AqfZ57EKbQq8+OXPxJ1qpAh+yOcQw=
Address (required)
- Description: IP address(es) assigned to the interface. Supports both IPv4 and IPv6, and multiple addresses can be specified, separated by commas.
- Purpose: Assigns IP addresses to the interface. These are the IPs that will be used within the VPN.
- Multiple Addresses: Supports multiple addresses for dual-stack IPv4/IPv6 setups.
- Example:
ini Address = 10.0.0.2/24, fd86:ea04:1115::1/64
ListenPort (optional)
- Description: The port on which the interface will listen for incoming WireGuard traffic. This is typically specified on servers.
- Purpose: Defines the port for incoming WireGuard traffic.
- Default Behavior: If not specified, WireGuard selects a random port.
- Firewall Considerations: Ensure this port is allowed through any firewalls.
- Example:
ini ListenPort = 51820
DNS (optional)
- Description: Specifies DNS server(s) to be used while the interface is up. Multiple DNS servers are separated by commas.
- Purpose: Sets DNS servers for name resolution while the interface is active.
- Client Configuration: Particularly useful for clients to resolve domain names over the VPN.
- Example:
ini DNS = 1.1.1.1, 8.8.8.8
MTU (optional)
- Description: Sets the Maximum Transmission Unit (MTU) for the interface. If not specified, WireGuard attempts to calculate an appropriate MTU.
- Purpose: Optimizes packet size to prevent fragmentation.
- Default Behavior: WireGuard auto-detects MTU, but manual setting can improve performance in some cases.
- Example:
ini MTU = 1420
PreUp, PostUp, PreDown, PostDown (optional)
- Description: Commands or scripts to execute before or after the interface is brought up or down. Useful for custom firewall rules or logging.
- Purpose: Automate tasks like configuring firewall rules or logging.
- Placeholders:
%ican be used as a placeholder for the interface name. - Example:ini
PostUp = Set-NetIPInterface -InterfaceAlias $env:WIRESOCK_TUNNEL_NAME -InterfaceMetric 0 (Set the metric to 0 for the virtual adapter after the connection is established)
Script execution timeout (optional)
- Description: The timeout of PreUp, PostUp, PreDown, PostDown scripts execution. The default value is 30 sec.
Virtual adapter mode (optional)
- Description: Virtual Adapter Mode can be configured per profile. If not set, the global configuration is used. See the Networking settings for more details.
Bypass LAN Traffic (optional)
- Description: Bypass LAN Traffic can be configured per profile. If not set, the global configuration is used. See the Networking settings for more details.
DPI protection
This section defines settings to evade or bypass Deep Packet Inspection (DPI) used by network operators, ISPs, or firewalls to detect, throttle, or block VPN traffic. Currently, WireSock Secure Connect implements two DPI protection techniques: Junk Packets and Magic Headers.
Junk Packets
Junk packets provide DPI protection for a standard WireGuard server by sending junk packets before the handshake, reducing detectability. Settings are controlled by Jc, Jmin, Jmax, and Jd (Jc, Jmin, and Jmax follow the AmneziaWG extension). Defaults: Jc = 3, Jmin = 50, Jmax = 1000, Jd = 0. If Jc is 0 or absent, no junk packets are sent.
Junk packet count (Jc)
- Description: Junk packet count (Jc) specifies the number of junk packets to send before the actual VPN session begins.
- Valid range: 0 to 200.
- Recommended value: Jc = 3-10.
- If Jc is set to zero then no junk packets are sent, and the protocol operates similarly to standard WireGuard.
Junk packet minimum size (Jmin)
- Description: Junk packet minimum size (Jmin) - defines the minimum byte sizes for each junk packet.
- Valid range: 0 to 1280.
- Jmin is typically set to 50 bytes.
Junk packet maximum size (Jmax)
- Description: Junk packet maximum size (Jmax) - defines the maximum byte sizes for each junk packet.
- Valid range: 0 to 1280.
- Jmax is typically set to 1000 bytes.
Junk packets delay (Jd)
- Description: Junk packets delay (Jd) - delay (in milliseconds) between junk packets sent before the handshake.
- Valid range: 0 to 200.
- Default value is 0
Magic Headers (AmneziaWG)
Magic Headers, a feature of the AmneziaWG protocol, improve obfuscation by adding random data to handshake packets and modifying WireGuard fields, making VPN traffic resemble other protocols. All parameters (S1, S2, H1, H2, H3, and H4) must be specified for Amnezia configuration. If both S1 and S2 are set to 0, no headers will be added.
NOTE
Important:
- Magic Headers must be set on both client and server and are incompatible with standard WireGuard servers.
- All parameters S1-S2, H1-H4 must not be empty to configure Magic Headers.
Init packet junk size (S1)
- Description: Init packet junk size (S1) determines the amount of random data appended to the initiation handshake packet, altering its size to evade detection.
- Valid range: 0 to 1280 bytes.
- A recommended range is between 15 and 150 bytes.
- If not specified, S1 defaults to 0, meaning no additional junk data is added.
Response packet junk size (S2)
- Description: Response packet junk size (S2) specifies the amount of random data added to the response handshake packet, modifying its size for obfuscation.
- Valid range: 0 to 1280 bytes. Ensure S1 + 56 ≠ S2 to maintain unpredictability.
- A recommended range is between 15 and 150 bytes.
- If not set, S2 defaults to 0, indicating no additional junk data is appended.
Init packet magic header (H1)
- Description: Init packet magic header (H1) sets a custom header for the initial handshake packet sent from the client to the server.
- Valid range: 1 to 4,294,967,295 (32-bit unsigned integer).
- Can be represented in various numerical formats, including hexadecimal.
- Each header (H1, H2, H3, H4) must be unique to prevent predictable sequences.
Response Packet Magic Header (H2)
- Description: IResponse Packet Magic Header (H2) defines a custom header for the handshake response packet sent from the server to the client.
- Valid range: 1 to 4,294,967,295 (32-bit unsigned integer).
- Can be represented in various numerical formats, including hexadecimal.
- Each header (H1, H2, H3, H4) must be unique to prevent predictable sequences.
Transport Packet Magic Header (H3)
- Description: Transport Packet Magic Header (H3) specifies a custom header for data packets transmitted during the VPN session.
- Valid range: 1 to 4,294,967,295 (32-bit unsigned integer).
- Can be represented in various numerical formats, including hexadecimal.
- Each header (H1, H2, H3, H4) must be unique to prevent predictable sequences.
Underload Packet Magic Header (H4)
- Description: Underload Packet Magic Header (H4) Sets a custom header for underload packets, which are specific control packets used within the AmneziaWG protocol.
- Valid range: 1 to 4,294,967,295 (32-bit unsigned integer).
- Can be represented in various numerical formats, including hexadecimal.
- Each header (H1, H2, H3, H4) must be unique to prevent predictable sequences.
Tunneled networks/addresses (required)
Defines which IP addresses are allowed to communicate with a given peer and determines the traffic that should be routed through the VPN tunnel. It acts as a routing table and access control list.
- Example:
0.0.0.0/0, ::/0routes all traffic (IPv4/IPv6) through the VPN. - Example:
192.168.1.0/24routes only traffic destined for the 192.168.1.0/24 network through the VPN; other traffic uses the default gateway (split tunneling).
NOTE
Tunneled networks/addresses is a mandatory parameter and cannot be empty. The default value is 0.0.0.0/0, ::/0, which routes all local traffic through the VPN tunnel.
Example of configuration:
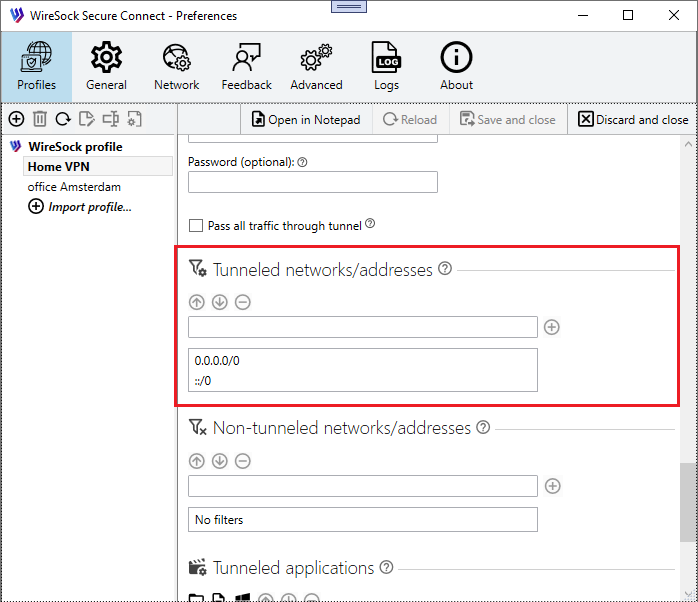
Type ip/network in the edit box and tap  to add it to the list of disallowed ips.
to add it to the list of disallowed ips.
Use the following buttons to move ip/networkip range up/down on the list of disallowed ips or delete it from the list:
 move ip/network up in the list of disallowed ips
move ip/network up in the list of disallowed ips move ip/network down in the list of disallowed ips
move ip/network down in the list of disallowed ips remove ip/network from the list of disallowed ips
remove ip/network from the list of disallowed ips
NOTE
You can use Tunneled networks/addresses and Tunneled applications at the same time, but their behavior follows an AND condition. This means that for traffic to be tunneled, it must match both of the following criteria:
- The destination IP address must be listed in Tunneled networks/addresses.
- The application generating the traffic must be listed in Tunneled applications.
Non-tunneled networks/addresses (Optional)
Identify IP addresses and ranges that should not use the VPN tunnel.
This parameter excludes specified IP addresses and ranges from the tunnel.
For example, if you want to access your local network,
you can exclude it from the tunnel by adding 192.168.1.0/24 to the Non-tunneled networks/addresses parameter.
NOTE
If Tunneled applications is configured, Non-tunneled networks/addresses will prevent the listed IPs and ranges from being tunneled for those applications.
Example of configuration:
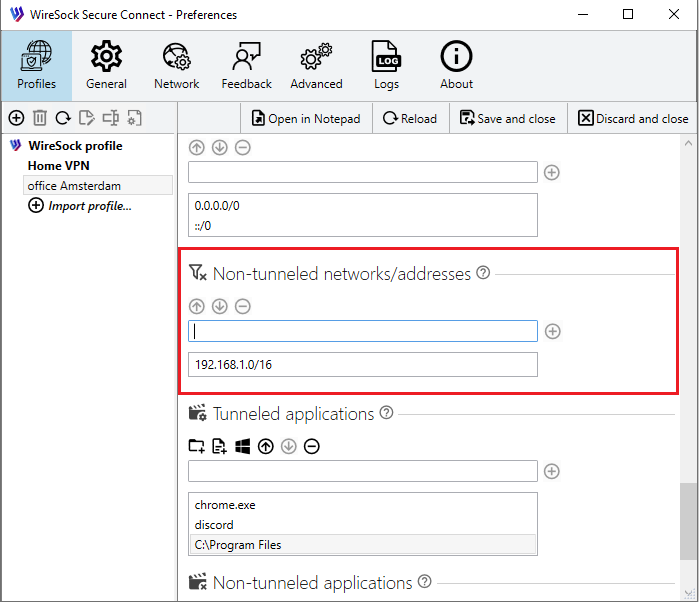
Type ip/network in the edit box and tap  to add it to the list of disallowed ips.
to add it to the list of disallowed ips.
Use the following buttons to move ip/networkip range up/down on the list of disallowed ips or delete it from the list:
 move ip/network up in the list of disallowed ips
move ip/network up in the list of disallowed ips move ip/network down in the list of disallowed ips
move ip/network down in the list of disallowed ips remove ip/network from the list of disallowed ips
remove ip/network from the list of disallowed ips
Tunneled applications (optional)
Define the applications that are authorized to use the VPN tunnel.
You can specify a process name, the full path to the application file on the filesystem, or the full path to a directory. It's not necessary to include the .exe extension for process names. If your entry includes slashes or backslashes, the system will recognize it as a full pathname. Providing a full pathname to a folder allows you to target that folder, automatically including all executables within it for convenience.
NOTE
If not set, the VPN tunnel is available to all applications.
Examples:
- Full path:
C:\Program Files (x86)\Google\Chrome\Application\chrome.exe - Process names:
discord, chrome, firefox - All applications in Program Files folder:
C:\Program Files
Dependency: Must be paired with Tunneled networks/addresses to define the scope of traffic for these applications.
NOTE
If WireSock Secure Connect is not running with elevated privileges (i.e., not as administrator), it can only tunnel applications that are launched by the current user.
Example of configuration:
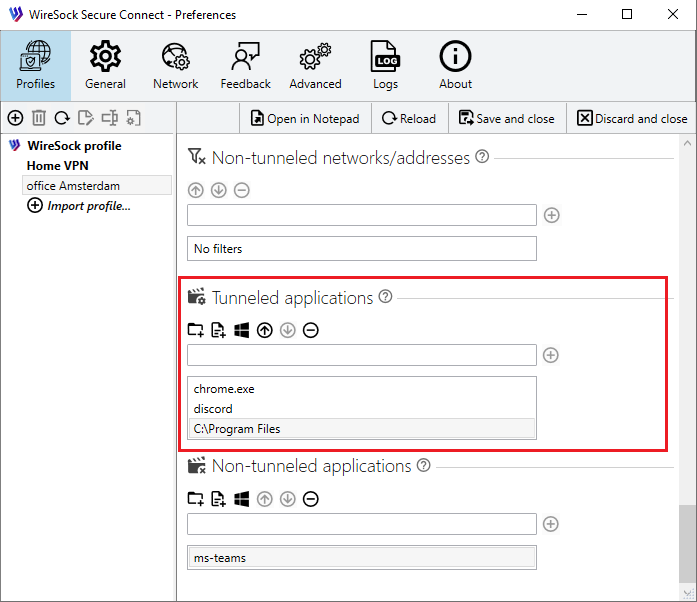
Type your application name in the edit box and tap to add it to the list of allowed apps or use the buttoms from toolbar:
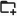 browse folder on the filesystem
browse folder on the filesystem browse application executable file on the filesystem
browse application executable file on the filesystem select running process name or path
select running process name or path
Use the following buttons to move application up/down on the list of allowed apps or delete it from the list:
 move application up in the list of allowed applications
move application up in the list of allowed applications move application down in the list of allowed applications
move application down in the list of allowed applications remove application from the list of allowed applications
remove application from the list of allowed applications
NOTE
You can use Tunneled networks/addresses and Tunneled applications at the same time, but their behavior follows an AND condition. This means that for traffic to be tunneled, it must match both of the following criteria:
- The destination IP address must be listed in Tunneled networks/addresses.
- The application generating the traffic must be listed in Tunneled applications.
Non-tunneled applications (Optional)
List the applications that are barred from using the VPN tunnel.
You can specify a process name, the full path to the application file on the filesystem, or the full path to a directory. It's not necessary to include the .exe extension for process names. If your entry includes slashes or backslashes, the system will recognize it as a full pathname. Providing a full pathname to a folder allows you to target that folder, automatically including all executables within it for convenience.
NOTE
If both Tunneled applications and Non-tunneled applications are specified, Tunneled applications is prioritized and evaluated first.
NOTE
If WireSock Secure Connect is not running with elevated privileges (i.e., not as administrator), it can only exclude applications from the tunnel if they are launched by the current user.
Examples:
- Full path:
C:\Program Files (x86)\Google\Chrome\Application\chrome.exe - Process names:
chrome, msoffice, firefox - All applications in Program Files folder:
C:\Program Files
Example of configuration:
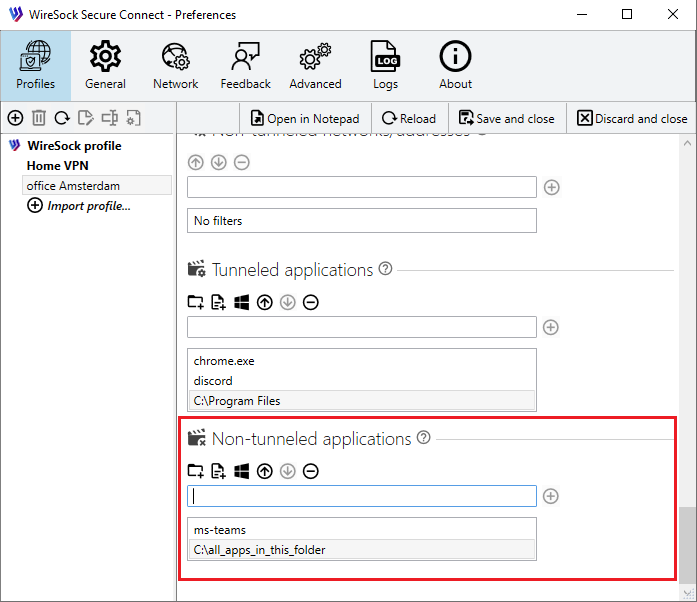
Type your application name in the edit box and tap  to add it to the list of disallowed apps or use the buttoms from toolbar:
to add it to the list of disallowed apps or use the buttoms from toolbar:
 browse folder on the filesystem
browse folder on the filesystem browse application executable file on the filesystem
browse application executable file on the filesystem select running process name or path
select running process name or path
Use the following buttons to move application up/down on the list of disallowed apps or delete it from the list:
 move application up in the list of disallowed applications
move application up in the list of disallowed applications move application down in the list of disallowed applications
move application down in the list of disallowed applications remove application from the list of disallowed applications
remove application from the list of disallowed applications
How WireSock Secure Connect handles tunneled and non-tunneled apps
WireSock Secure Connect determines whether a process is tunneled based on the tunneled apps and non-tunneled apps lists in the following order:
- If both tunneled apps and non-tunneled apps are undefined (empty), traffic from all processes is tunneled.
- If a process matches tunneled apps, all its traffic is tunneled.
- If a process matches non-tunneled apps, its traffic is excluded from the tunnel.
- If a process does not explicitly match either list, one of the following applies:
- If tunneled apps is undefined/empty and non-tunneled apps contains specific exclusions, the application is tunneled.
- If non-tunneled apps is undefined/empty and tunneled apps contains specific inclusions, the application is not tunneled.
- If both tunneled apps and non-tunneled apps are defined (mixed policy), the application is not tunneled unless explicitly included to tunneled apps.
SOCKS5 Proxy
For users needing to route their WireGuard handshake through a SOCKS5 proxy, additional parameters are provided:
- Socks5Proxy: Set the SOCKS5 proxy endpoint, e.g.,
socks5.sshvpn.me:1080or an IP-based endpoint like13.134.12.31:1080. - Socks5ProxyUsername: (Optional) Specify the proxy username.
- Socks5ProxyPassword: (Optional) Specify the proxy password.
- Socks5ProxyAllTraffic: (Optional) When set to
true(e.g.,Socks5ProxyAllTraffic = true), it forces all WireGuard traffic through the SOCKS5 proxy, effectively masking it from DPI detection.